We often say that at Cyrex, our team live and breath cybersecurity and it’s no exaggeration! Our security engineers often seek out bug bounties and other challenges to support their ongoing careers and cybersecurity efforts. In this ongoing series, we’ll dive into some of the write-ups from our security engineers and show you a little of the talent that makes up our incredible team. First up, Hazem Elsayad! Lead Offensive Security Engineer, 2023 was a very successful year for him during his out-of-hours bug bounty hunting. Let’s take a look at one of his write-ups, which covers a bug bounty where a “subdomain takeover lead to a full account takeover”.
Introduction
In this blog post, I will walk you through the discovery of a critical vulnerability discovered on redacted.com. This vulnerability allowed me to take over any user's account by exploiting a subdomain takeover, which led to account takeovers due to the shared ASP session across all subdomains. Moreover, I will emphasize the importance of patience and persistence in bug hunting, which ultimately led me to claim the maximum bounty.The Discovery
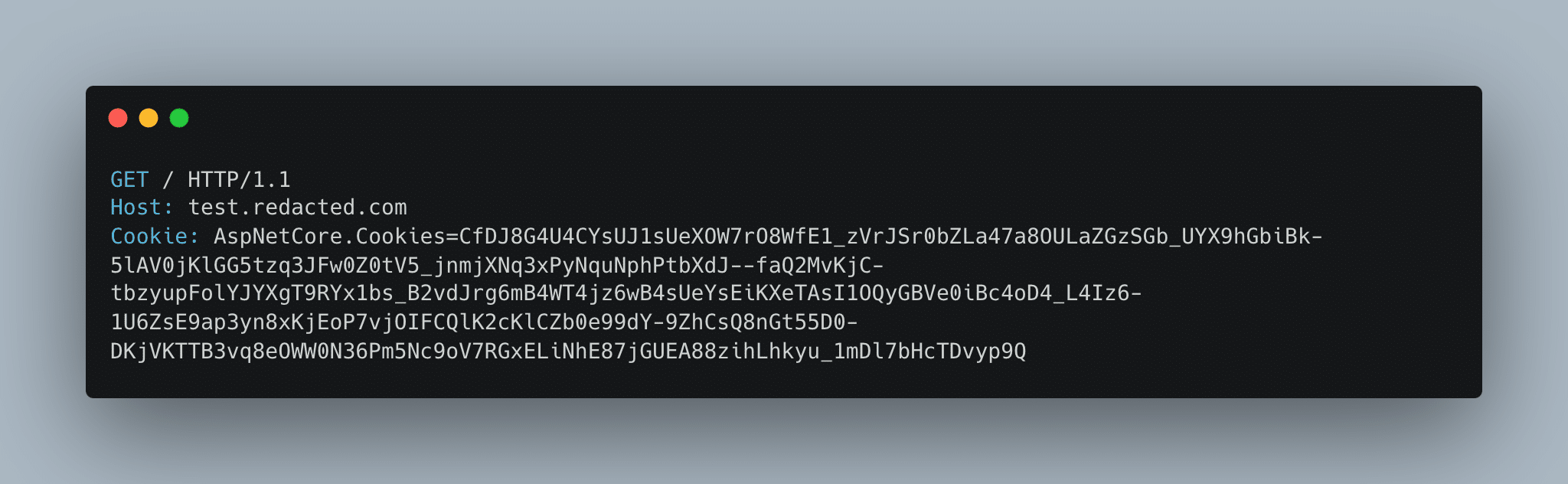
It all started when I was hacking on the main domain and after I logged in, I noticed that the AspNetCore.Cookies was being shared in my requests. Everywhere, across all other subdomains of the main domain. By that time, I realized that I only needed to find a subdomain takeover to take over other users' accounts. Then stumbled upon a subdomain takeover vulnerability in test.redacted.com. This subdomain was pointing to test-redacted.azurewebsites.net, and with the help of godiego blog post about Subdomain Takeover in Azure I managed to claim it.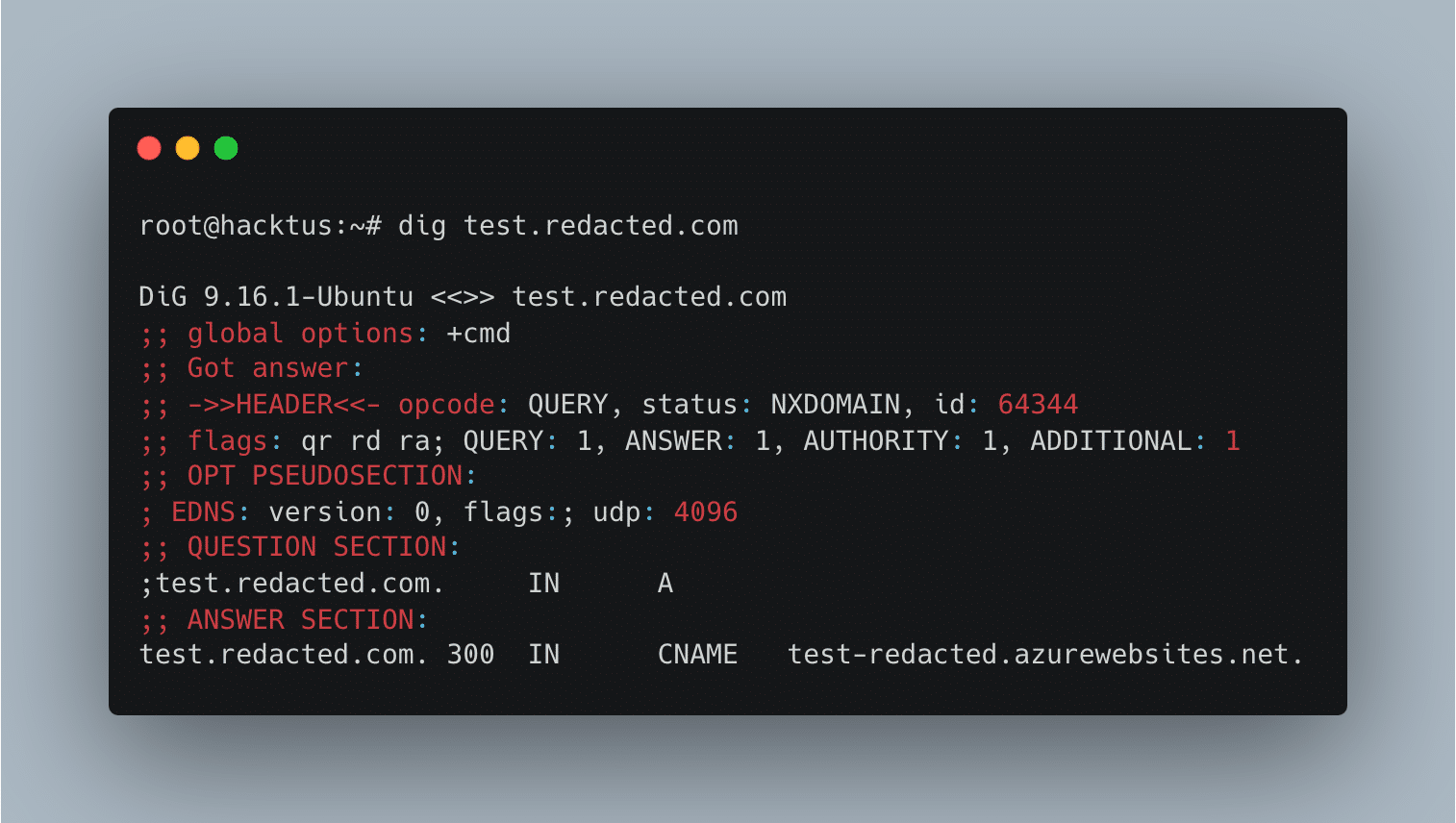 Then I navigated to the claimed subdomain and checked the logs and found that my cookies were logged there. Eventually, I was able to take over anyone's account if they navigated to test.redacted.com/.
Then I navigated to the claimed subdomain and checked the logs and found that my cookies were logged there. Eventually, I was able to take over anyone's account if they navigated to test.redacted.com/.
The Impact
An attacker exploiting this vulnerability could take over any user's account by navigating them to their claimed subdomain and accessing their sensitive information through the shared ASP session. This can result in unauthorized access, data theft, and other malicious activities.Conclusion
This blog post highlights the importance of understanding and securing subdomains, as well as the potential risks associated with misconfigurations. In this case, the subdomain takeover vulnerability led to account takeovers due to the shared ASP session. If I rushed to report this vulnerability as a normal STO bug, I was going to end up with a medium/high report with a bounty of $500-1500, Instead, I dug further to get the most impact out of it before reporting.Timeline
- Reported: January 30, 2023, 7:40pm
- Fixed: January 30, 2023 9:52pm
- Severity: Critical (9.5)
- Bounty: 3000$